4e7f244190c6ffbf7b20443e3e69cf2402c4268a
privacy.sexy
Privacy & security generator tool for Windows.
because privacy is sexy 🍑🍆
In this repo you find:
- Application & infrastructure code of privacy.sexy, simply everything is code & open-sourced.
- Fully automated CI/CD pipeline to AWS for provisioning serverless infrastructure using GitHub actions.
- Vue.js application in conjunction with domain-driven design, event-driven architecture & data-driven programming.
Commands
- Setup and run
- For development:
npm installto project setup.npm run serveto compile & hot-reload for development.
- Production (using Docker):
- Build
docker build -t undergroundwires/privacy.sexy . - Run
docker run -it -p 8080:8080 --rm --name privacy.sexy-1 undergroundwires/privacy.sexy
- Build
- For development:
- Prepare for production:
npm run build - Run tests:
npm run test:unit - Lint and fix files:
npm run lint
Extend scripts
Fork it & add more scripts in src/application/application.yml and send a pull request 👌
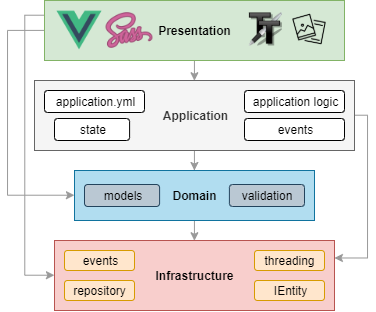
Architecture
Application
- Powered by TypeScript + Vue.js 💪
- and driven by Domain-driven design, Event-driven architecture, Data-driven programming concepts.
- Application uses highly decoupled models & services in different DDD layers.
- Domain layer is where the application is modelled with validation logic.
- Presentation Layer
- Consists of Vue.js components & UI stuff.
- Event driven as in components simply listens to events from the state and act accordingly.
- Application Layer
- Keeps the application state
- The state is a mutable singleton & event producer.
- The application is defined & controlled in a single YAML file (see Data-driven programming)
- Keeps the application state
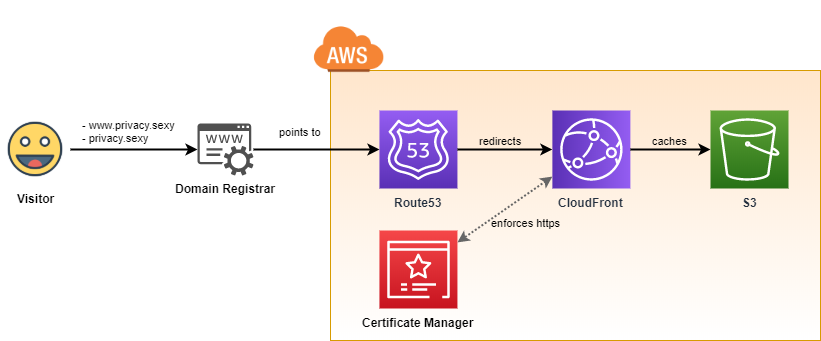
AWS Infrastructure
- The application runs in AWS 100% serverless and automatically provisioned using CloudFormation files and GitHub Actions.
- Maximum security & automation and minimum AWS costs were the highest priorities of the design.
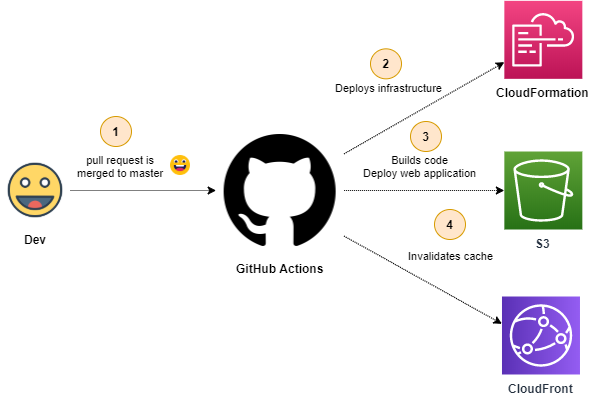
GitOps: CI/CD to AWS
- Everything that's merged in the master goes directly to production.
- Deploy infrastructure ► Deploy web application ► Invalidate CloudFront Cache
- See more at build-and-deploy.yaml
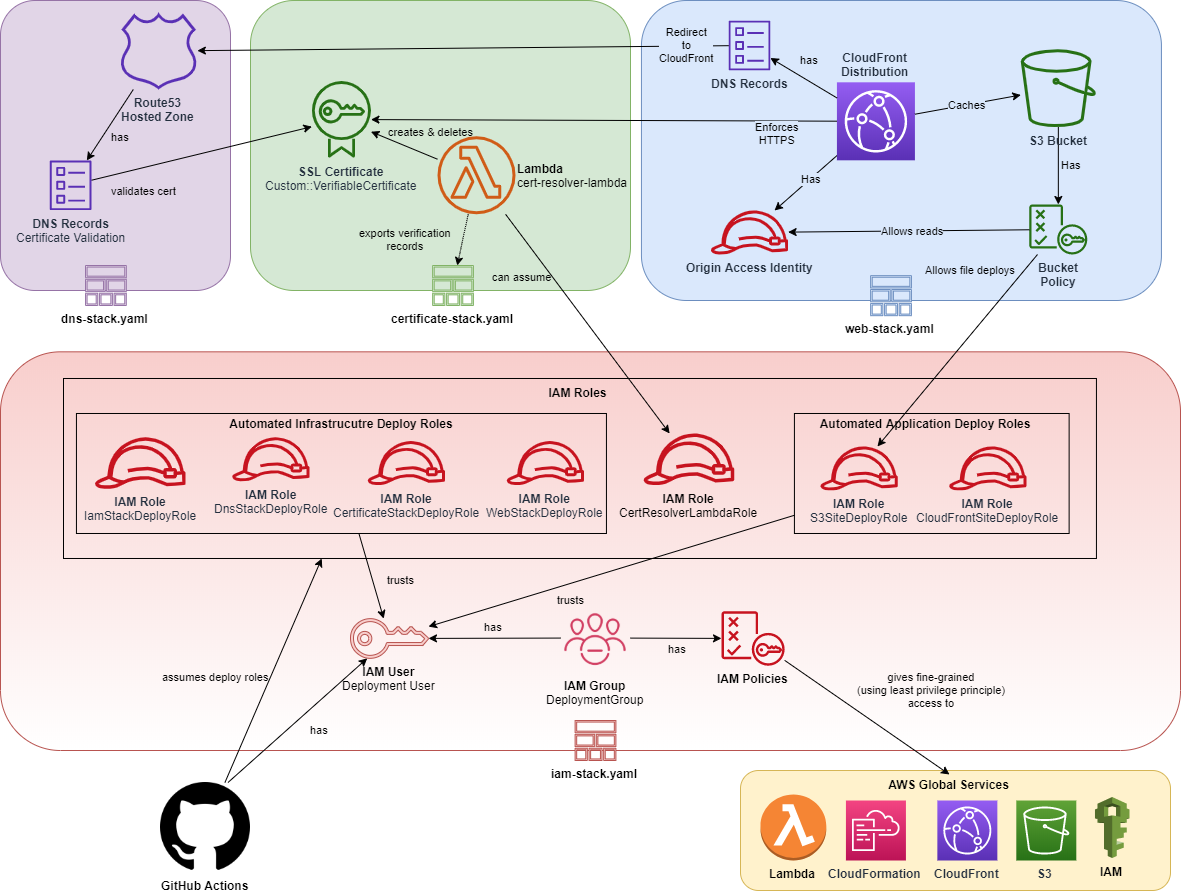
CloudFormation
- AWS infrastructure is defined as code with following files:
iam-stack: Creates & updates the deployment user.- Everything in IAM layer is fine-grained using least privileges principle.
- Each deployment step has its own temporary credentials with own permissions.
certificate-stack.yaml- It'll generate SSL certification for the root domain and www subdomain.
- ❗ It must be deployed in
us-east-1to be able to be used by CloudFront byweb-stack. - It uses CustomResource and a lambda instead of native
AWS::CertificateManager::Certificatebecause:- Problem:
- AWS variant waits until a certificate is validated.
- There's no way to automate validation without workaround.
- Solution:
- Deploy a lambda that deploys the certificate (so we don't wait until certificate is validated)
- Get DNS records to be used in validation & export it to be used later.
- Problem:
web-stack.yaml: It'll deploy S3 bucket and CloudFront in front of it.dns-stack.yaml: It'll deploy Route53 hosted zone- Each time Route53 hosted zone is re-created it's required to update the DNS records in the domain registrar. See Configure your domain registrar.
- I use cross stacks instead of single stack or nested stacks because:
- Easier to test & maintain & smaller files and different lifecycles for different areas.
- It allows to deploy web bucket in different region than others as other stacks are global (
us-east-1) resources.
Initial deployment
- ❗ Prerequisite: A registered domain name for website.
-
Configure build agent (GitHub actions)
- Deploy manually
iam-stack.yamlwith stack nameprivacysexy-iam-stack(to follow the convention)- It'll give you deploy user. Go to console & generate secret id + key (Security credentials => Create access key) for the user IAM users.
- 🚶 Deploy secrets:
- Add secret id & key in GitHub Secrets.
AWS_DEPLOYMENT_USER_ACCESS_KEY_ID,AWS_DEPLOYMENT_USER_SECRET_ACCESS_KEY
- Add more secrets given from Outputs section of the CloudFormation stack.
- Add secret id & key in GitHub Secrets.
- 🚶 Deploy secrets:
- Run GitHub actions to deploy rest of the application.
- It'll run
certificate-stack.yamland theniam-stack.yaml.
- It'll run
- It'll give you deploy user. Go to console & generate secret id + key (Security credentials => Create access key) for the user IAM users.
- Deploy manually
-
Configure your domain registrar
- ❗ Web stack will fail after DNS stack because you need to validate your domain.
- 🚶 Go to your domain registrar and change name servers to NS values
dns-stack.yamloutputs those in CloudFormation stack.- You can alternatively find those in Route53
- When nameservers of your domain updated, the certification will get validated automatically, you can then delete the failed stack in CloudFormation & re-run the GitHub actions.
Thank you for the awesome projects 🍺
- Vue.js the only big JavaScript framework that's not backed by companies that make money off your data.
- liquor-tree for the awesome & super extensible tree component.
- Ace for code box.
- FileSaver.js for save file dialog.
- chai & mocha for making testing fun.
- js-yaml-loader for ahead of time loading
application.yml - v-tooltip takes seconds to have a tooltip, exactly what I needed.
Description
Open-source tool to enforce privacy & security best-practices on Windows, macOS and Linux, because privacy is sexy
bloatwarebloatware-removalcleanupcybersecuritydebloatdebloaterdebotnetdomain-driven-designlinuxmacosprivacyprivacy-protectionprivacy-toolssecuritysecurity-hardeningsecurity-toolsecurity-toolstweaks-collectionwindows10windows11
Readme
32 MiB
Languages
TypeScript
91.5%
Vue
6.3%
JavaScript
0.9%
SCSS
0.8%
Python
0.4%